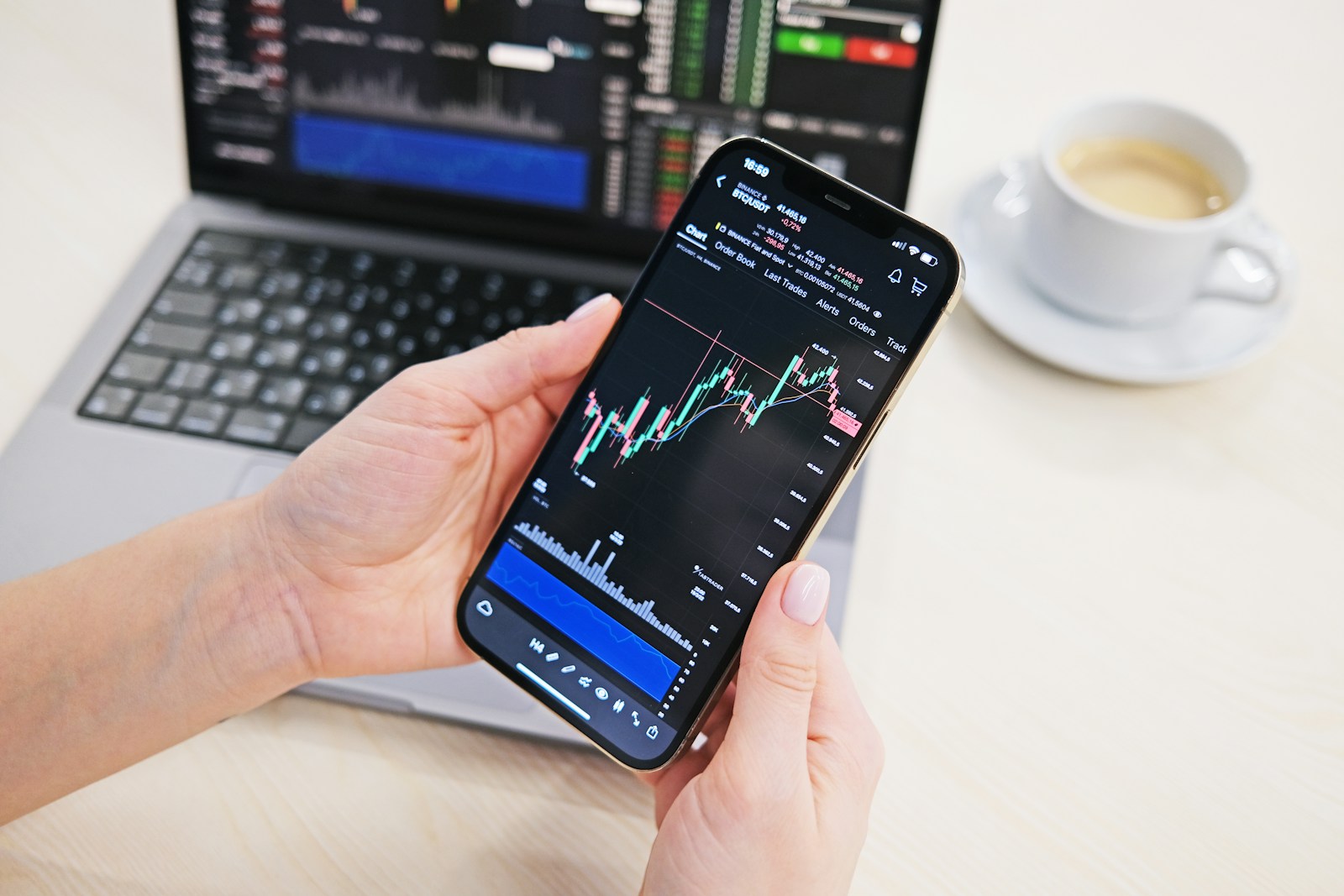
Effective identification of illicit transfers within decentralized ledgers relies on advanced chain analysis tools that map transaction flows across multiple addresses. Recent investigations reveal that over 70% of unauthorized asset movements can be tracked through clustering algorithms combined with heuristics derived from exchange interactions. These methods enable pinpointing intermediary custodians and potential cash-out points, which are crucial for recovery efforts.
Address examination requires in-depth scrutiny of transaction histories, timestamps, and smart contract interactions to establish links between suspicious accounts. For example, the 2023 Axie Infinity breach demonstrated how forensic teams leveraged temporal patterns and mixer detection to follow the path of approximately $600 million in diverted tokens. Such cases highlight the importance of combining automated analytics with manual review to overcome obfuscation techniques.
Challenges persist due to privacy-enhancing protocols like CoinJoin or zero-knowledge proofs, which complicate tracing attempts by fragmenting transactional data. Nevertheless, integrating on-chain data with off-chain intelligence–such as IP logs, KYC records from centralized platforms, and social engineering insights–amplifies investigative effectiveness. How these hybrid approaches evolve will dictate future success rates in asset restitution amid shifting regulatory frameworks and escalating technical countermeasures.
Wallet forensics: tracing stolen cryptocurrency funds [Wallet & Security security]
Identifying the movement of pilfered digital assets requires a meticulous approach combining blockchain transparency with sophisticated analysis tools. Public ledger data allows investigators to track token transfers across addresses, but the challenge lies in correlating these with real-world entities. Effective examination hinges on clustering algorithms that group associated addresses, revealing transaction patterns and potential cash-out points.
One notable example involves the 2021 Poly Network breach, where over $600 million was illicitly moved through multiple chains. Analysts utilized cross-chain transaction mapping and tagged known mixer services to pinpoint intermediary wallets. This enabled law enforcement agencies to freeze some assets before conversion into fiat currencies, demonstrating how timely investigative efforts can facilitate partial recovery.
Technical scrutiny extends beyond mere transaction tracking; behavioral analysis plays a pivotal role. By examining spending velocities, withdrawal habits, and interaction with decentralized exchanges or privacy-enhancing platforms like Tornado Cash, specialists infer laundering attempts. Real-time monitoring systems equipped with heuristics alert analysts when suspicious clusters emerge, enabling proactive countermeasures against asset dispersion.
In terms of methodology, leveraging graph theory algorithms complements traditional forensic techniques. Constructing directed acyclic graphs from transaction flows helps isolate sink nodes–addresses where value accumulates without further outgoing transactions–which often represent endpoints controlled by perpetrators. Identifying these hubs informs subsequent legal procedures or negotiation strategies aimed at fund restitution.
Challenges arise when adversaries deploy obfuscation techniques such as coin mixing, chain hopping, or use of privacy-focused blockchains like Monero or Zcash. Despite this, multi-layered analytics combining on-chain metadata with off-chain intelligence–such as IP logs from exchange providers–enhance attribution accuracy. Collaboration between blockchain analytics firms and regulatory bodies has increasingly resulted in successful interdictions and asset recoveries.
Future developments promise integration of machine learning models trained on historical breach data to predict malicious activity paths before significant losses occur. While absolute prevention remains elusive due to pseudonymity features intrinsic to distributed ledgers, continuous improvement in analytical frameworks ensures higher probabilities of identifying culprits and recovering misappropriated tokens within complex crypto ecosystems.
Identifying Suspicious Wallet Addresses
To detect potentially illicit addresses, analysts primarily rely on comprehensive blockchain investigation tools that map transaction histories and behavioral patterns. Anomalies such as rapid movement of assets through multiple intermediary accounts or frequent interactions with darknet marketplaces often serve as red flags. For example, in a recent case involving over $50 million diverted through mixers, the key to identification lay in recognizing clusters of addresses exhibiting consistent cyclical transactions within short timeframes.
Address classification is further refined by combining on-chain data with off-chain intelligence–such as exchange blacklists and known scam databases. Advanced clustering algorithms group related accounts based on transaction graph analysis, revealing hidden ownership structures. This technique was crucial during the 2023 “Phantom” exploit investigation, where researchers traced fragmented asset flows across thousands of nodes before pinpointing the originators for potential recovery efforts.
Behavioral Patterns and Transaction Analysis
Suspicious entities tend to demonstrate specific transactional behaviors like rapid fund dispersion immediately after receipt or repeated attempts to obfuscate origins via chain hopping between various blockchains. Monitoring temporal transaction density helps highlight these activities. For instance, unusual spikes in outgoing transfers following an influx of tokens can indicate laundering attempts aimed at complicating forensic tracing.
Identification also hinges on analyzing interaction history with flagged platforms or services under regulatory scrutiny. Addresses consistently engaging with high-risk mixers or decentralized exchanges lacking KYC protocols raise suspicion levels significantly. Incorporating heuristics based on transaction fees, gas price anomalies, and nonce irregularities further sharpens investigative accuracy.
- High-frequency micro-transactions consolidating into a single output address;
- Repeated splitting and merging of inputs suggesting layering;
- Use of privacy-enhancing tools such as coinjoin mechanisms;
- Engagement with newly created or dormant smart contracts exhibiting minimal legitimate activity.
The interplay between these factors informs a risk scoring model crucial for prioritizing targets during forensic audits and facilitating asset retrieval operations.
While automated systems provide initial detection frameworks, human expertise remains indispensable in contextualizing raw blockchain data within broader threat intelligence feeds. Analysts must discern false positives arising from legitimate high-volume traders or institutional custodians employing complex strategies from genuinely illicit actors deliberately attempting to evade surveillance. This nuanced differentiation was demonstrated in a 2022 study where machine learning models achieved 87% precision but required manual validation to exclude benign cases effectively.
The continuous evolution of blockchain ecosystems demands adaptive methodologies that integrate multi-source data streams for comprehensive wallet scrutiny. Proactive collaboration between industry stakeholders enhances the ability to disrupt illicit networks swiftly while maximizing asset recovery prospects amidst growing complexity and scale of digital asset misappropriation schemes.
Analyzing blockchain transaction patterns
Effective investigation of asset movements within decentralized ledgers requires detailed examination of transactional flows and address behaviors. Identifying recurring transfer sequences, clustering addresses based on interaction frequency, and recognizing mixing services are crucial for reconstructing the path of misappropriated digital assets. For example, in a 2023 case involving over $15 million diverted through multiple chain hops, analysts used temporal correlation and input-output analysis to isolate intermediary clusters that facilitated obfuscation. Such granular pattern recognition accelerates the process of pinpointing key nodes for potential recovery efforts.
Transaction graph analytics leverage both on-chain metadata and heuristic models to detect anomalous activities indicative of illicit reallocations. By applying algorithms that track UTXO consolidation or splitting strategies–commonly employed to evade detection–investigators can infer control relationships between addresses. A notable instance involved tracking a sequence where 1,200 BTC were moved in batches averaging 100 BTC every three hours, revealing an operator’s attempt to mimic legitimate trading volumes. This level of detail supports constructing accurate behavioral profiles necessary for subsequent legal or remedial action.
Techniques and tools for forensic analysis
Specialized software platforms integrate clustering heuristics with machine learning classifiers to enhance the precision of transaction tracing across multiple blockchains. These tools analyze patterns such as round-trip transactions, chain hopping via wrapped tokens, and interactions with known exchange deposit addresses. For example, during the investigation of a cross-chain fraud scheme in early 2024, combining entity attribution databases with real-time mempool monitoring allowed analysts to intercept suspicious transfers before they reached liquidity pools. This proactive approach exemplifies how dynamic analysis improves chances for asset retrieval.
Comparative assessment also plays a significant role when examining divergent transaction patterns across different blockchain protocols. While UTXO-based chains like Bitcoin exhibit distinct input-output structures facilitating traceability, account-based systems like Ethereum require attention to smart contract interactions and event logs. Case studies demonstrate that integrating these methodologies yields comprehensive insights; one study showed that layering ERC-20 token transfers with native coin movement data uncovered hidden circular flow designed to launder over $5 million worth of tokens within days. Ultimately, combining protocol-specific techniques enhances overall investigative robustness.
Using Clustering Techniques for Wallet Analysis
Effective recovery of illicit asset flows on blockchain networks relies heavily on clustering algorithms that group addresses sharing control or behavioral patterns. These techniques significantly enhance the ability to link multiple accounts to a single entity, thereby enabling more comprehensive investigation pathways. For example, heuristic methods such as common-input ownership allow analysts to identify clusters by examining transactions where multiple inputs originate from the same operator, which is often indicative of shared control over those accounts.
Clustering is particularly valuable when addressing cases involving misappropriated digital assets. By aggregating related addresses, investigators reduce the complexity inherent in tracing scattered outputs across decentralized ledgers. Notably, in the 2021 Poly Network breach, clustering helped map thousands of addresses involved in laundering operations, guiding law enforcement towards eventual partial asset recovery and seizure.
Mechanisms and Methodologies Behind Clustering
At its core, clustering exploits transaction graph analysis combined with machine learning models trained to detect patterns consistent with single-entity control. Algorithms utilize heuristics such as transaction co-spending and address reuse while also integrating temporal and value flow correlations. Modern approaches incorporate unsupervised learning techniques like DBSCAN or k-means to detect dense subgraphs that represent tightly knit account groups.
However, sophistication varies across blockchains; UTXO-based systems like Bitcoin provide clearer heuristics compared to account-based ledgers like Ethereum, where smart contracts complicate clustering due to shared contract wallets and proxy interactions. To overcome this challenge, layered analysis incorporating both on-chain data and off-chain intelligence–such as exchange deposit information–enables more accurate cluster attribution.
The efficacy of these methods directly impacts tracing accuracy during investigations into financial misconduct or cyber thefts involving tokens. Clustering not only accelerates identification but also mitigates false positives by cross-validating connections within complex transaction webs. This precision is critical when coordinating with regulatory bodies or orchestrating multi-jurisdictional asset recovery efforts.
Practical deployment of clustering tools has evolved alongside growing blockchain transaction volumes and sophistication of laundering schemes. Platforms like Chainalysis Reactor or CipherTrace employ proprietary clustering combined with real-time monitoring to flag suspicious activity promptly. As networks scale and anonymization techniques mature–such as mixers or coinjoins–the continual refinement of clustering algorithms remains pivotal for maintaining investigative relevance amid evolving adversarial tactics.
Leveraging open-source tracing tools
Effective recovery of illicitly appropriated digital assets relies heavily on the use of open-source blockchain analysis utilities. These instruments enable detailed investigation into transaction histories and address clusters, offering critical insights that proprietary software might overlook. For instance, tools like GraphSense and BlockSci provide granular data extraction from public ledgers, facilitating pattern recognition essential for identifying movement of misappropriated tokens across multiple networks.
One notable case involved tracing approximately $50 million in unlawfully transferred tokens through Ethereum’s network. By applying open-source solutions such as Etherscan’s API alongside graph-based heuristics, analysts successfully mapped out intermediary addresses and smart contract interactions. This multi-layered approach highlighted the value of combining raw blockchain data parsing with heuristic-driven clustering algorithms to reconstruct comprehensive asset flows during forensic examinations.
Technical capabilities and comparative advantages
The core advantage of community-developed tracing frameworks lies in their transparency and adaptability. Unlike closed commercial platforms, these tools permit customization to accommodate emerging blockchain protocols or novel obfuscation techniques used by illicit actors. For example, Bitquery, an open API aggregator, supports cross-chain analysis by indexing transactions from Bitcoin, Binance Smart Chain, and others simultaneously–crucial for investigations where stolen reserves transit through decentralized exchanges or mixers.
A technical comparison reveals that while proprietary products may offer user-friendly dashboards and automated reporting, open-source alternatives empower investigators with access to raw query languages (e.g., GraphQL) and scripting environments such as Python or Rust. This flexibility enables bespoke workflows tailored to specific investigative hypotheses or compliance requirements. Moreover, engagement with active developer communities ensures continuous improvement aligned with real-time adversarial tactics seen in laundering schemes.
Integrating these open resources into forensic methodologies enhances the precision of fund flow reconstruction by enabling triangulation between on-chain indicators and off-chain intelligence sources. When combined with machine learning classifiers trained on transaction metadata patterns, this approach significantly increases the probability of pinpointing illicit asset repositories or exit points within complex decentralized finance ecosystems currently under scrutiny due to volatile market conditions and regulatory pressures.
Reporting Findings to Authorities: Strategic Insights and Future Directions
Providing law enforcement with comprehensive, actionable intelligence on illicit asset movements requires integrating deep transaction examination with blockchain ledger scrutiny. Detailed mapping of compromised account activity, combined with clustering heuristics and temporal pattern recognition, enhances the probability of successful intervention and subsequent restitution efforts.
For example, in a recent case involving approximately $12 million diverted through multiple decentralized exchanges, linking wallet identifiers to known mixing services proved pivotal. This analysis not only exposed laundering circuits but also supported cross-jurisdictional collaboration by furnishing verifiable cryptographic proofs embedded within immutable blockchain records.
Key Considerations for Effective Reporting
- Data Accuracy and Granularity: Delivering high-fidelity transaction trails enriched with metadata–timestamps, gas fees anomalies, and smart contract interaction logs–enables authorities to reconstruct event sequences precisely.
- Contextual Correlation: Overlaying on-chain data with off-chain intelligence such as IP address logs or exchange KYC details strengthens attribution confidence and legal admissibility.
- Automation vs. Expert Review: While automated tools accelerate initial detection, nuanced human interpretation remains essential for discerning complex obfuscation tactics like chain hopping or token swaps.
The broader implications extend beyond individual incidents. As regulatory bodies worldwide enhance their technical capabilities, the demand for standardized forensic reporting formats grows. Initiatives like the Interpol Cryptocurrency Reporting Framework seek to harmonize evidence presentation, facilitating swifter judicial processes globally.
Looking ahead, incorporating artificial intelligence models trained on vast blockchain datasets promises predictive insights that can preemptively flag suspicious activities before significant value displacement occurs. Additionally, advances in zero-knowledge proof protocols could offer new avenues for privacy-preserving disclosures to authorities without compromising user confidentiality.
Ultimately, bridging analytical precision with strategic communication transforms raw ledger data into compelling narratives that empower recovery operations and reinforce deterrence mechanisms across financial ecosystems vulnerable to illicit expropriation.