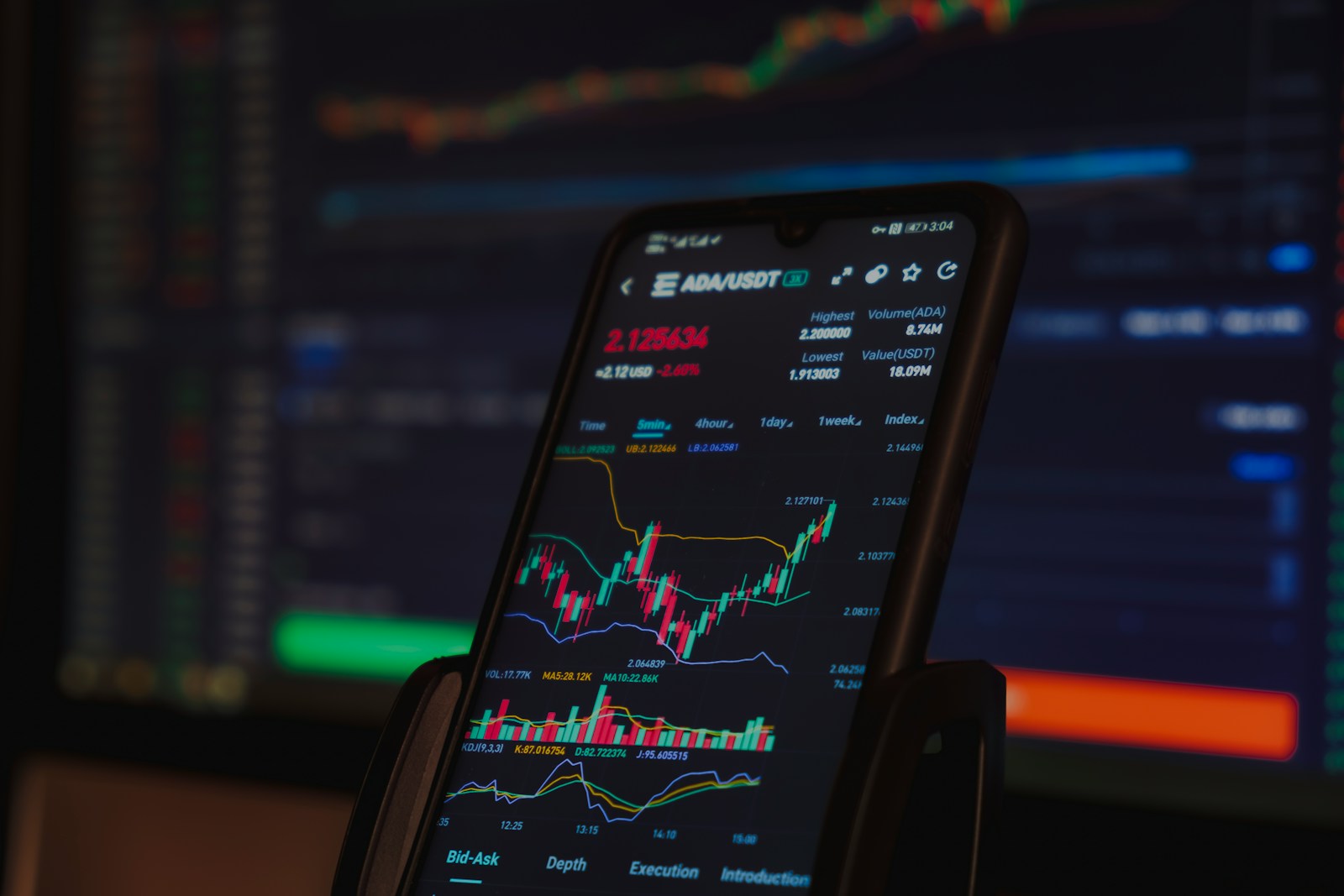
Concentration of computational power within a handful of dominant pools directly challenges Nakamoto’s vision of a trustless and distributed network. Currently, the top five mining entities control over 60% of the total hashing capacity on Bitcoin’s blockchain, raising concerns about potential collusion and censorship risks. Quantifying this spread goes beyond simple percentages–examining variance in pool sizes, geographical dispersion, and ownership transparency reveals layers of centralization that raw data alone might mask.
Tracking the allocation of processing strength provides critical insight into network resilience against attacks such as 51% takeovers or protocol manipulation. For instance, when a single pool surpasses 30% dominance, it triggers alarms within the community because it tips the balance away from decentralized consensus. Recent shifts in market conditions saw certain Asian-based pools rapidly expand their share to nearly 40%, while smaller independent operations struggle to maintain footing amid rising hardware costs and energy price fluctuations.
Evaluating distribution metrics requires combining block propagation times with statistical models that factor in hash rate volatility and miner migration patterns. This approach highlights how some participants may temporarily boost output through rented equipment or cloud services, skewing short-term readings without reflecting lasting decentralization improvements. Understanding these dynamics assists developers and stakeholders in crafting protocols that incentivize diversification rather than consolidation.
Does reliance on large conglomerates threaten the foundational security assumptions? Evidence suggests so. Historical cases like the GHash.io episode in 2014 demonstrated how near-monopoly control spurred voluntary reduction pledges to restore balance. Today’s landscape demands continuous monitoring tools equipped with granular analytics capable of discerning not just who holds power but how transient or entrenched that power is across competing factions.
Hashrate distribution: measuring mining decentralization [Mining & Staking mining]
The geographic allocation of computational power directly impacts the resilience and security of blockchain networks. Concentration of resources in specific regions often leads to vulnerabilities, such as susceptibility to regulatory crackdowns or infrastructure failures. Recent data indicates that a handful of countries still dominate, with China historically accounting for over 60% before recent policy shifts, while the United States now holds approximately 38% according to the Cambridge Centre for Alternative Finance (CCAF) in early 2024.
Evaluating the spread of processing capacity requires more than just raw numbers; it involves understanding how these figures translate into influence over block validation and consensus mechanisms. Staking operations, which rely on token holdings rather than pure computational output, introduce another layer where capital concentration can skew governance. For instance, Ethereum’s transition to proof-of-stake revealed that a small percentage of validators control a significant portion of staked ETH, highlighting centralization risks beyond pure computational metrics.
Technical insights into concentration metrics
One effective way to quantify network dispersion is through the application of concentration indices like the Herfindahl-Hirschman Index (HHI). Applying this measure to Bitcoin’s operational nodes reveals an HHI above 0.2 in some months, signaling moderate market power held by dominant mining pools. Entities such as Foundry USA and AntPool have consistently controlled substantial shares exceeding 15% each at various intervals throughout 2023. Such dominance raises questions about Nakamoto’s original vision of distributed trust across independent participants.
Geographic clustering also introduces latency and censorship risks. For example, concentrated operations within regions prone to power outages or political intervention can disrupt transaction validation. The 2021 Chinese shutdown exemplified this effect when roughly half of global computational throughput vanished overnight, causing temporary network instability. Conversely, diversification across continents–North America, Europe, Central Asia–enhances fault tolerance and mitigates systemic risks inherent in single-region dependence.
Staking-based ecosystems present different challenges but similar patterns emerge regarding ownership concentration. On networks like Cardano or Solana, staking pools dominate voting power disproportionately relative to individual delegators’ stakes. This dynamic complicates governance decentralization despite technically distributed hardware resources. Monitoring validator node distribution alongside stake-weighted influence provides a fuller picture of overall ecosystem health.
In conclusion, accurate assessment demands combining multiple parameters: geographic dispersion indices, pool size variances, operator independence levels, and stakeholder diversity across both proof-of-work and proof-of-stake models. Continuous tracking enables stakeholders to identify emerging centralization trends promptly and implement countermeasures such as incentivizing smaller operators or promoting multi-jurisdictional deployments–thus preserving Nakamoto consensus principles foundational to blockchain integrity.
Analyzing hashrate concentration metrics
Quantifying the extent to which computational power is consolidated among entities is fundamental for assessing network robustness. The Nakamoto coefficient, a metric derived from the minimum number of participants controlling over 50% of the total processing capability, offers a clear indicator of susceptibility to collusion or censorship. For example, Bitcoin’s Nakamoto coefficient typically hovers around 4 to 6, reflecting that half of its work capacity lies within a handful of mining pools. This level of aggregation prompts questions about resilience against coordinated attacks.
Examining individual contributors reveals variations in their share of operational throughput. Some large-scale pools command upwards of 25-30% each, a pattern observed not only in Bitcoin but also in Ethereum Classic and Litecoin networks. Such dominance can distort consensus dynamics and incentivize strategic behavior affecting block validation times and reward distribution. Detailed analysis requires tracking pool switching behaviors and temporary hashrate spikes during market shifts or hardware deployments.
Concentration measurement techniques and their implications
Beyond the Nakamoto coefficient, the Herfindahl-Hirschman Index (HHI) provides granularity by squaring participant shares before summation, thus penalizing disproportionate dominance more heavily. Recent data from Bitcoin mining pools show an HHI fluctuating between 0.12 and 0.18, indicating moderate aggregation but still below monopoly thresholds commonly recognized in antitrust contexts (above 0.25). Applying HHI across multiple blockchains exposes differing competitive landscapes; for instance, networks with smaller economies tend to exhibit higher index values due to fewer active pools.
Operational transparency also influences concentration assessments. Pools vary in reporting accuracy regarding their actual control over hashing resources versus proxies or rented capacity from cloud services. This discrepancy complicates precise calculations and necessitates cross-referencing on-chain evidence with off-chain declarations. Notably, instances where a single operator controls multiple pool identities artificially inflate decentralization metrics unless carefully accounted for.
Historical case studies reveal how shifts in equipment availability affect power dispersion. The surge in ASIC miner deployments in mid-2023 led to significant reshuffling among top performers on Bitcoin’s network, temporarily increasing centralization as new entrants consolidated resources before spreading out again through mergers or splits. Conversely, Ethereum’s transition to proof-of-stake drastically altered the landscape by removing hashing competition altogether, underscoring how protocol changes directly impact computational resource allocation patterns.
Understanding these dynamics assists stakeholders in designing incentives that discourage excessive centralization while fostering healthy competition among operators. Encouraging smaller entities through reduced entry barriers or protocol adjustments–such as variable difficulty algorithms–can improve equilibrium states. Moreover, monitoring real-time metrics enables proactive detection of anomalies potentially signaling cartel formation or systemic vulnerabilities threatening network security.
Tools for tracking miner locations
Network monitoring platforms like BTC.com and Blockstream.info provide granular insights into the geographic allocation of hashing power by analyzing connection points and latency data from different mining farms. These services utilize IP mapping combined with pool identification to estimate where significant computational efforts originate. For instance, recent analytics revealed that a substantial portion of global operations remains concentrated in East Asia, predominantly China, affecting the overall spatial balance of mining activity. Such tools enable stakeholders to observe shifts in operational clusters as regulatory environments evolve or new infrastructure emerges.
Complementing this, pool-level statistics offer valuable indicators of resource clustering by revealing the proportion of work attributed to individual operators within their network. Services like MiningPoolStats aggregate miner submissions and correlate them with known server locations, helping to approximate regional dominance without direct access to physical sites. This method highlights how certain pools command a large share of processing capability, raising concerns about potential vulnerabilities linked to centralization in limited territories.
An increasingly sophisticated approach involves integrating blockchain data with third-party telemetry that tracks IP routing patterns and Autonomous System Numbers (ASNs). Solutions such as Nansen Analytics and custom-built geolocation algorithms assign mining nodes to specific countries or data centers based on network topology and observed traffic behavior. In 2023, these methods successfully identified emergent hubs outside traditional strongholds, including North America and Scandinavia, diversifying the landscape beyond previous concentrations. However, precision depends heavily on miners’ willingness to disclose accurate information and the effectiveness of obfuscation techniques they might employ.
The challenge remains balancing transparency with privacy since many operators mask their true positions through VPNs or proxy servers, complicating exact localization efforts. Nevertheless, combining multiple datasets–like pool share reports, real-time node responsiveness tests, and ISP registries–enhances reliability when assessing how dispersed computational resources are globally. Observing changes over time also reveals how geopolitical shifts impact operational distribution; for example, recent crackdowns have led some entities to relocate facilities internationally, thereby altering regional proportions significantly within months.
Impact of Pool Dominance on Security
Concentration of computational power within a limited number of mining entities poses tangible risks to network integrity. When a single pool or a small group controls over 50% of the overall processing capacity, the theoretical possibility of executing a Nakamoto consensus attack arises, undermining transaction finality and trust in the protocol. For instance, historical data from Bitcoin’s ecosystem highlights moments when pool dominance exceeded this critical threshold, sparking community alerts and prompting redistribution efforts.
Geographic centralization further exacerbates vulnerability by clustering significant computational resources within specific regions. This geographic concentration creates susceptibility to regulatory crackdowns, infrastructure failures, or coordinated state-level interventions that could disrupt operations simultaneously across multiple major pools. The 2021 mining migration following China’s ban illustrated how sudden shifts in geographic hubs directly impacted global operational stability and network latency.
Analyzing control shares reveals uneven allocation among top mining conglomerates, with some pools commanding more than 30% individually. Such concentration complicates the measurement of effective decentralization since nominally independent pools may share underlying ownership or hardware providers. This hidden centralization can amplify collusion potential and reduce resilience against coordinated manipulation attempts, undermining Nakamoto’s vision of distributed trustlessness.
Contrastingly, fragmented participation across numerous smaller entities enhances resistance to majority attacks by diluting influence over block validation processes. However, an excessively dispersed environment might introduce inefficiencies such as increased orphan rates or delayed block propagation due to network topology constraints. Thus, balancing concentration with dispersion remains a nuanced challenge requiring continuous monitoring through sophisticated analytical tools tracking real-time operational metrics.
The security implications extend beyond mere percentages; pool policies around block acceptance and transaction selection also shape attack surfaces. Pools adhering strictly to protocol rules limit exploit vectors compared to those adopting custom consensus parameters or enabling selfish mining strategies. Case studies involving Ethereum Classic forks demonstrated how diverging pool incentives can lead to chain splits or temporary instability despite relatively balanced resource distribution.
In conclusion, evaluating the interplay between dominant pools’ market share and their geographic positioning is crucial for assessing systemic risk levels accurately. Stakeholders should prioritize transparency initiatives encouraging disclosure of mining infrastructure ownership alongside promoting diversity in node locations globally. Continuous vigilance combined with adaptive governance mechanisms will fortify network robustness against threats stemming from concentrated computational authority.
Conclusion: Evaluating Stake vs Proof-of-Work Node Dispersion
Stake-based consensus exhibits a markedly different pattern of resource aggregation compared to Nakamoto-style computation validation. While staking often concentrates voting power within a handful of dominant pools, the geographic and operational spread tends to be less fragmented than the sprawling mining setups scattered globally. For instance, Ethereum’s shift to proof-of-stake demonstrated that nearly 70% of total stake is controlled by fewer than ten entities, signaling potential centralization risks despite eliminating massive energy consumption.
The computational power model remains heavily influenced by pool consolidation and regional hardware clusters, especially in areas with cheap electricity like Kazakhstan or Texas. Recent data shows that over 60% of cumulative computational output is funneled through five major pools, indicating a persistent concentration challenge. This clustering impacts network resilience and raises questions about how effectively Nakamoto’s original vision of distributed trust is upheld in practice.
Broader Implications and Future Trajectories
- Decentralized Pool Architectures: Innovations such as multi-party computation (MPC) in staking pools can dilute control without sacrificing efficiency, potentially reshaping token-holder influence patterns.
- Geographic Diversity Incentives: Both paradigms could benefit from protocol-level encouragements for nodes outside conventional hotspots, offsetting current geographic concentration trends seen in ASIC-dense regions or validator-centric jurisdictions.
- Hybrid Models: Emerging networks exploring hybrid consensus mechanisms might balance the extremes of resource centralization inherent in pure proof-of-work or proof-of-stake models, combining their strengths while mitigating weaknesses.
The choice between stake-driven and computation-heavy validation affects not only immediate participation dynamics but also long-term governance structures and security assurances. Measuring node dispersion should extend beyond raw numbers to incorporate qualitative factors such as pool governance transparency and cross-jurisdictional regulatory exposure. Ultimately, maintaining the integrity envisioned by Nakamoto demands continuous scrutiny of concentration vectors–whether they arise from token accumulation or hashing capacity–and adaptive protocol designs that anticipate shifts in market forces and technology.







